HackTheBox - APKey (android lab)
So after a long time I decided to get back into blogging. Writing doesn’t come to me very instinctively, so I kept on pushing the task of writeups or documenting my learning journey.
This is going to be a writeup of a Hack the Box challenge from the Mobile category - APKey. I solved this challenge a couple of months back, and it was an easy challenge.
Static Analysis
As usual, I fired up jadx-gui to get an idea about the source code and mainly android_manifext.xml.
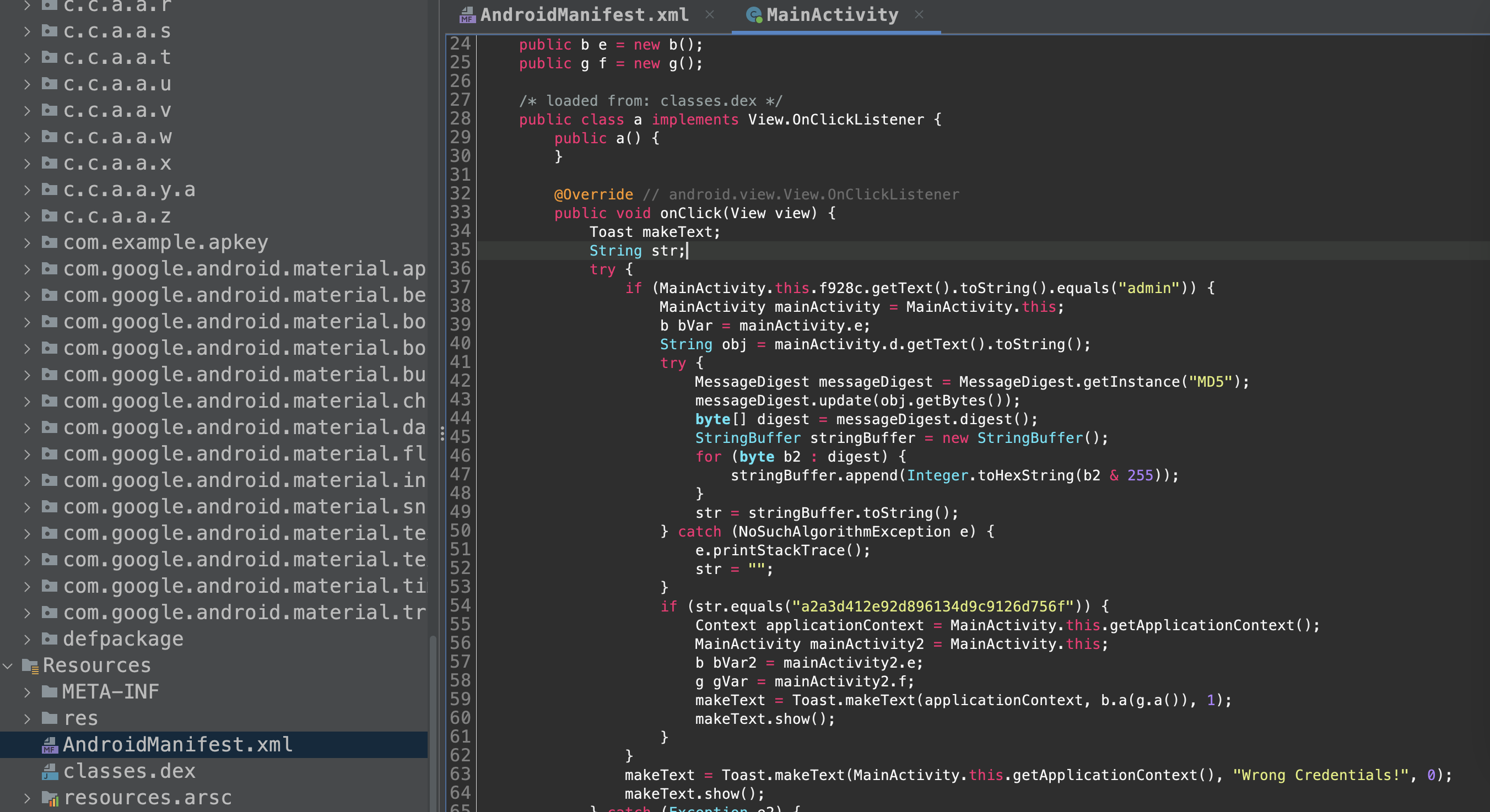
There was nothing much in the manifest file, also looks like a little bit of obfuscation was done as we can see the class names being renamed. Next I went right to the main activitiy - com.example.apkey.MainActivity.
1
2
3
4
5
6
7
8
public void onCreate(Bundle bundle) {
super.onCreate(bundle);
setContentView(R.layout.activity_main);
this.f927b = (Button) findViewById(R.id.button);
this.f928c = (EditText) findViewById(R.id.editTextTextPersonName);
this.d = (EditText) findViewById(R.id.editTextTextPassword);
this.f927b.setOnClickListener(new a());
}
From this it can be understood that there are 2 text fields - one for PersonName (or username) and then for password and a button. This is mostly a login functionality with the credential check.
Now let’s look at working of the Mainactivity.
It can be seen that in the if condition, the username f928c string value is compared with the string "admin". If this condition is true, the following happens :
- The string value inside password is copied to to obj and an MD5 hash is done on it.
- This value is matched with
"a2a3d412e92d896134d9c9126d756f"and if this results to true, the content of maketest is displayed as a short duration notification.
If the condition fails, it exists the previous if and displayed “Wrong Credentials” as notification in the application context.
Method 1
The first method I thought was to use an online md5 hash decrypter. But as anticipated, it did not work.
Method 2 - Patching
I first tried to reverse the function which generated the flag, that is, to reverse the functions being called : makeText = Toast.makeText(applicationContext, b.a(g.a()), 1);
After a couple of minutes, I understood that there should be another way to do this.
Either get the value using dynamic analysis or patching. As I was not adept at using frida hooking, thought the best way to proceed was to patch the hash to a known value.
I opened the MainActivity$a.smali in an editor and searched for the hash value.
The changed it to the md5 hash of a dummy string - "admin" - 21232f297a57a5a743894a0e4a801fc3 and saved it.
Now we have to recompile, sign and then run the apk and hopefully that will display the flag.
To compile, I used this command - apktool b APKey -o newapk.apk
To sign the apk, I found a bunch of tools after reading online :
1
2
keytool -genkey -v -keystore my-release1.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release1.keystore newapk1.apk alias_name
These worked for me and then I uninstalled the old apk and installed the patched one.
1
2
adb uninstall "com.example.apkey"
adb install newapk.apk
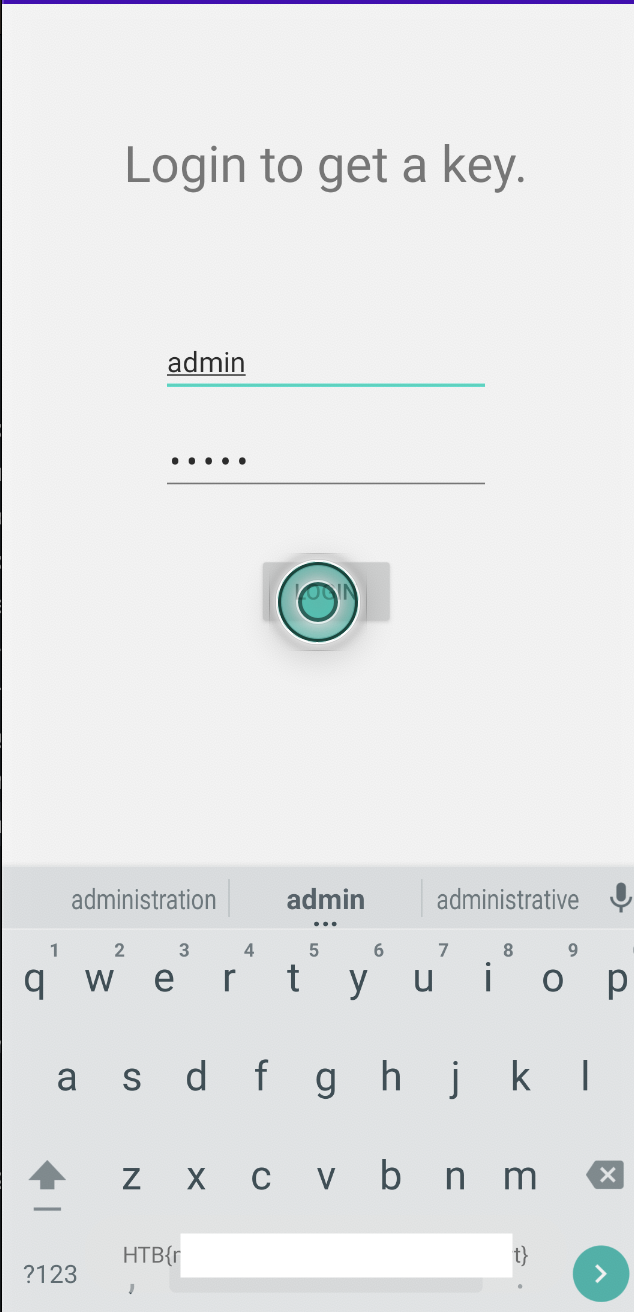
Getting the flag
Open the apk and enter the credentials admin : admin and the flag is displayed.
I learnt patching and the use of keytool and jarsigner to sign the apk and hence this was very interesting for me.