WhiteHat 2k18 – re06
WhiteHat came just after the Hackon CTF. I did not try the challenge during the CTF.
But then the challenge was quite decent. It was a .net binary.
About the binary:
The binary was .net so I decided to use ILSpy to disassemble it. It was written in C#.
The disassembled code was very clear and easy to debug. It looks like this: 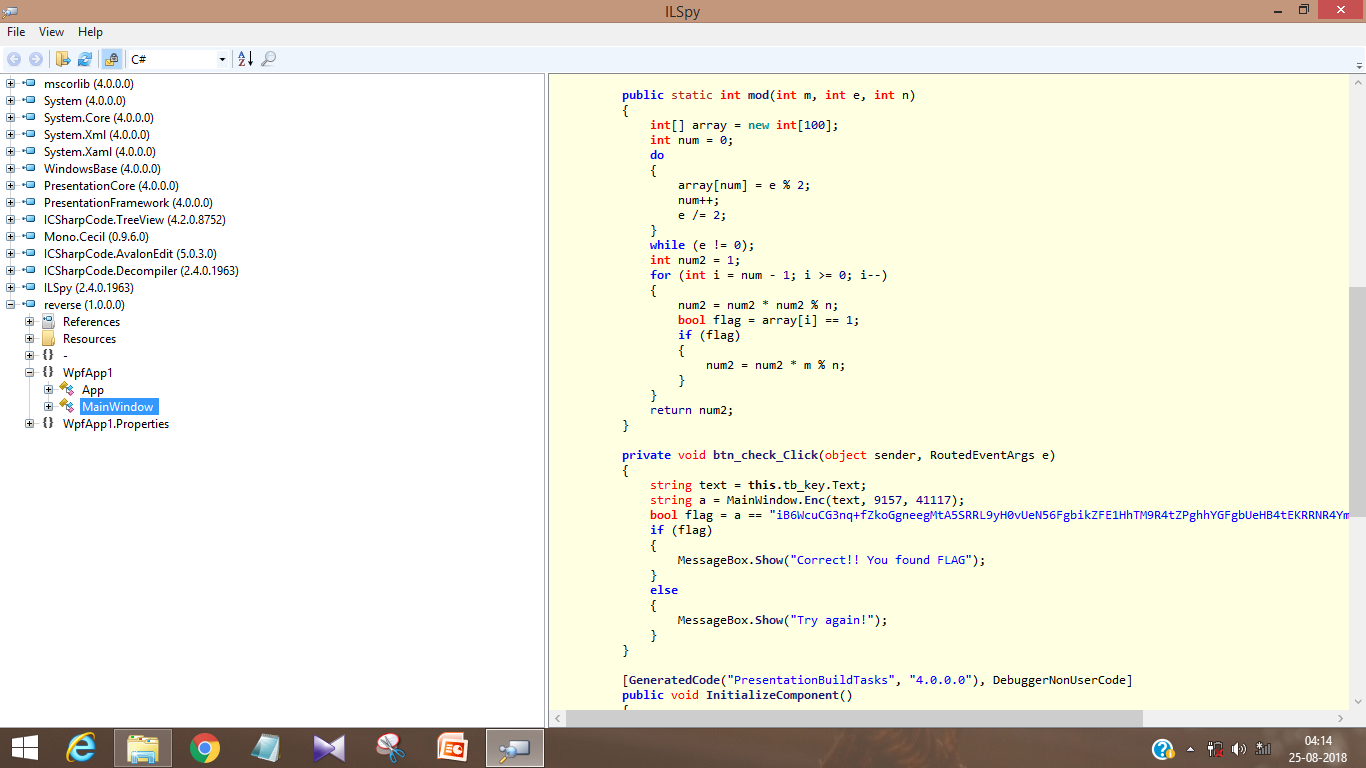
The input string was first Encrypted using the function Enc and then finally encoded using base64.
The function Enc was taking each letter from the string, converting it to its corresponding ascii value. Then comes the role of a simple straightforward RSA in it.
The Enc function:
n was given , e was given encrypted text was also given. There can be different approaches from this point. My approach was a simple one. The life-saver… Brute-force.
I decoded the base64 and then took each char from that.
I took each printable character and encoded with the Enc function and checked with the above b64 decoded char.
If it matched, append it to the flag.
And that’s it. You got your flag.
Python code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
import base64
string='iB6WcuCG3nq+fZkoGgneegMtA5SRRL9yH0vUeN56FgbikZFE1HhTM9R4tZPghhYGFgbUeHB4tEKRRNR4Ymu0OwljQwmRRNR4jWBweOKRRyCRRAljLGQ='
dec=base64.b64decode(string).decode('UTF-16LE')
new=''
import string
l='!@_{}'
chars=string.letters+ string.digits+l
def encode(s,e,n):
array=[]
while(e!=0):
array.append(e%2)
e/=2
num2=1
for i in range(len(array)-1,-1,-1):
num2=num2*num2%n
if(array[i]==1):
num2=num2*ord(s)%n
return num2
flag=''
for i in dec:
for j in chars:
var=encode(j,9157,41117)
if(var==ord(i)):
flag+=j
print flag
Flag:
WhiteHat{N3xT_t1m3_I_wi11_Us3_l4rg3_nUmb3r}